Can someone hack into my phone through WiFi: How to prevent?
Can someone hack into my phone through WiFi?
Our smartphones contain every element of our life and might constitute a potential threat by disclosing our most sensitive information to data hackers.
So, almost nothing is more essential than keeping your phone safe.
If you want some basic information on how to reduce your chances of getting hacked as well as ways to fix a hacked router, read this post all the way to the conclusion!
Let’s get started!

Someone hack into my phone through Wifi
Can someone hack into my phone through WiFi?
The answer is YES.
Someone can undoubtedly hack into your phone over WiFi.
Not only over WiFi, but also through any other internet connection you might use.
Your phone was most likely hacked from the manufacturer.
Can someone hack into my phone through WiFi?
Furthermore, every phone contains a microphone and camera that can be turned into espionage equipment by someone who knows how.
Cybercriminals are growing more inventive in their methods of stealing your information, therefore you should study how your phone might be hacked via your WiFi network.
You can learn how your phone can be compromised over your WiFi network and how to protect against this by reading this quick guide.
How can someone hack into my phone through WiFi?
Yes, hackers can use WiFi networks to obtain access to a mobile phone (Android or iOS).
Hackers typically use Man In The Middle attacks, also known as DNS Hijacking, to enter WiFi networks.

How can someone hack into my phone through WiFi?
iOS and Android Threats
A hacker needs to install malware on your phone in order to hack it via WiFi or other channels (such as mobile data).
Malware is an abbreviation for malicious software, which is especially designed to cause harm or allow unauthorized access.
It can be preloaded by the manufacturer as a back door for them or their government agencies, or it can be installed by the user, who is duped into thinking it is a harmless piece of software.
In rare circumstances, a hacker can utilize security flaws in the operating system or popular programs to install and run malware on a user's computer.
iOS and Android Threats
-
iOS malware does exist, but there is no method to detect it because applications do not have authorization to scan the system. It is just not viable to create antivirus software for iOS. Other malware for iOS is available, but Pegasus is one of the most dangerous.

Pegasus spyware
-
Android phones are susceptible to infection right when they’re out of the box.
It is well known and widely reported that both American and Chinese-made mobile phones are sent to clients with preloaded spyware designed to gather and communicate user data to a distant server.
Even without government intervention, the situation is the same.
There is a ton of malware hiding everywhere, as well as a ton of hoaxes made to persuade the user to download the program and provide the hacker unrestricted access to private information.
Read more | Can your parents see your search history on wifi
WiFi Hacking and MITM Attacks
A hacker can gain access to your phone by using the MITM (Man in the Middle) attack.
If you have a cable, DSL, or fiber-optic network in your home or workplace, you must have a router to transfer signals.
The router links all of your devices to the internet, including phones, PCs, and smart home devices.
It is fairly simple for a hacker to deploy by utilizing your router as bait.

WiFi Hacking and MITM Attacks
In layman's terms, this is how an MITM attack works:
-
Your device is linked to a WiFi router.
-
The router sends the MAC address, which identifies your device, to your device. Each device on the local network has a distinct MAC address.
-
The hacker discovers the target local WiFi router and obtains access to the target router's MAC address.
-
Then the hacker modifies his device's MAC address to match the MAC address of the target router.
-
At this point, every device on the local WiFi network is linked to the hacker's device.
-
As the MITM, the hacker transfers data between the router and his device.
When this happens, the hacker gains access to all inbound and outgoing network requests using various data collecting methods.
This means that whatever information you provide on a website, such as a login and password or credit card information, is saved on the hacker's device.
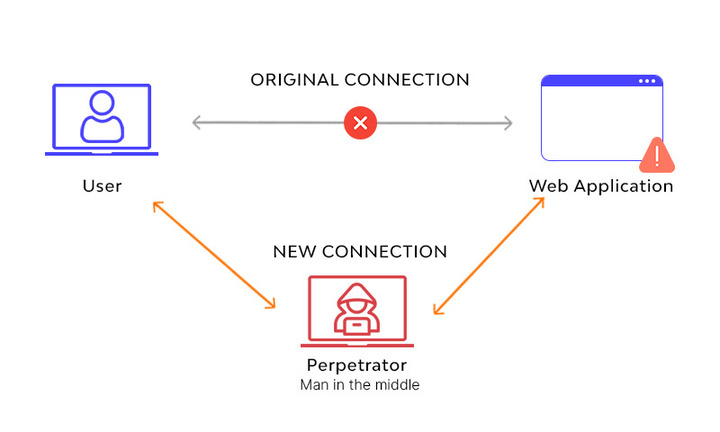
Every device on the local WiFi network is linked to the hacker's device.
Furthermore, every URL you visit is saved.
All of your devices linked to the hijacked WiFi network, including your phone, are compromised.
It's vital to understand that your phone can be hacked over any WiFi network, including your own and public networks.
Note: Be cautious while connecting to a new network since hackers keep suspicious WiFi networks open in order to get into devices and gain sensitive information.
How to know you’ve been hacked?
To find out whether your router has been hacked, there are signs to check for. You can detect it by checking for the following signs.

How to know you’ve been hacked?
Your username and password become invalid
It's not a good sign when passwords suddenly stop working.
This is not an exception when it comes to your router.
If the WiFi network password or login information for the router's admin panel are no longer valid, it may be a sign that a hacker has gained access to your router and changed the settings to prevent you from using it.

Your username and password become invalid
Unknown device connected to your Wifi network
If you see an unusual IP address (especially one from another country), it is very likely that a hacker has obtained access to your network.
Look for any strange IP addresses as our second technique of verifying whether your router has been hacked.
How to locate unknown WiFi router-connected devices:
-
Launch a web browser.
-
In the address bar, you enter your router’s IP address.
-
To access the router dashboard, enter your username and password (can be found at the back of your router).
-
After logging in, check for the "connected devices" or "attached devices" option.
-
Examine the list of WiFi network-connected devices.
-
If you see an unexpected device connecting to your router, block its MAC address.

Unknown device connected to your Wifi network
Note: If you discover an unexpected device or observe that more devices are linked to your network than there are in your house, you must act quickly.
Redirected to malicious websites
Another sign of a hacked router is when you try to browse your typical websites and are constantly redirected to sites you did not plan to visit.
This is a classic symptom of DNS hijacking or MITM.
When you notice this happening with clean websites in your regularly visited history, raise the alert.
Ransomware messages
Ransomware is a type of malicious software used by hackers to block you from accessing your data in exchange for a ransom payment.
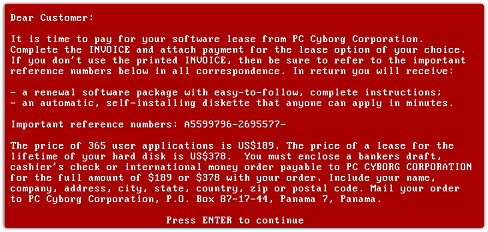
Ransomware messages
If a hacker obtains access to your router, they may quickly prohibit network access.
But what if you get an email or other form of communication from a hacker asking for money in exchange for network access?
The government advises against paying the ransom and suggests reporting the incident to the police department's cyber cell.
How to minimize risks of being hacked?
If you don't mind major firms and governments spying on you for "your own good," be extremely cautious when selecting your next mobile device.

How to minimize risks of being hacked?
-
When installing software on your device, utilize reliable sources and check user reviews before downloading and installing anything you'll regret later.
-
When utilizing the internet outside of your home network, use VPN software or a browser with built-in VPN functionality.
-
Change the router's default username and password on your home network to make it more difficult for hackers to penetrate.
Read more | Can i use my own router with centurylink
How to fix a hacked router?
These are the procedures you must carry out in order to repair your network and restore your devices' safety if it shows indicators of being hacked.
-
Reset your router
-
Disconnect from the Internet
-
Change passwords
-
Turn off remote management
-
Update router firmware
-
Fix your affected phone
Reset your router
If you perform a factory reset, your router's settings and passwords will be reset. There should be a physical reset button on the back of your router to help you with this operation.
You'll find a physical reset button on the back of your router to help you with this process.

Reset your router
Here's how to reset your router:
-
Keep your router plugged into a power source.
-
Locate the router's reset button. It is typically seen on the back or bottom.
-
For 30 seconds, use a paperclip or a needle to press the reset button.
-
After 30 seconds, release the button.
-
Allow the router to restart.
Disconnect from the Internet
When you disconnect your router from the internet, the hacker loses access to the router because the link is broken.
Although this process is simple, it is one of the first things you need to try because it can have a big effect on this problem.

Disconnect from the Internet
Change passwords
After rebooting your router, log in to the admin interface and reset the password.
Remember that resetting your router will reset your login information to the factory default username and password.
The account and password are often shown on your router's label for reference.

Change passwords
How to Change the Password on a Router:
-
Open your favourite web browser and input your router's IP address.
-
Log in the router control panel with the default username and password.
-
Go to the settings menu.
-
Change password for Router
-
Enter the new password.
-
Save your modifications.
When changing your password, choose a unique and difficult password that includes unusual characters such as (! . $ &).
You should also reset the admin panel settings on your router.
Turn off remote management
You should block external network access to your router. Here are how to do it:
-
Open the router's administration panel.
-
Go to Settings => Remote Management.
-
Disable Remote Management and save your change.
You should also take further action to prevent hackers by doing the following step.
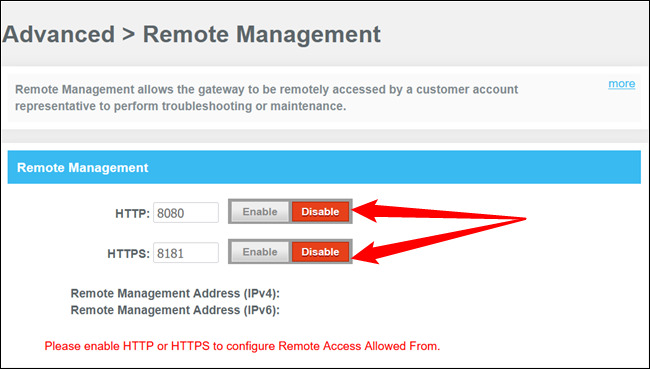
Turn off the remote management
Update router firmware
Routers do not often update automatically, which is why it is necessary to change the firmware manually.
Firmware is software that controls several aspects of your router and its hardware.
Upgrades are essential since they aid in the resolution of vulnerabilities, which might be a tempting target for a hacker looking to get access to your router.
To upgrade, go to Router Settings => Firmware Upgrade => Download & Install, and that's all there is to it.
Update router firmware
Fix your affected phone
After you've repaired your router, it's time to inspect and repair your phone.
-
Go to Phone Settings > About Phone > Factory Reset.
-
Change your login information for banking applications, social networking apps, and other services.
-
Do not use public WiFi.
Factory reset
Other important tips:
As you move forward with a more security-conscious mindset, here are a few more precautions to prevent illegal access in the future:
-
Change your router's credentials every three months.
-
Regularly update router firmware.
-
In the router dashboard, monitor connected devices.
-
Make use of a "guest network" for your house guests.
Conclusion
Following this guide, you can understand the issue and evic the hacker to recover control of your network and phone security. And hope that our response to the question "Can someone hack into my phone through WiFi?" was helpful for you!


2 Comments
Oscar Smith
Totally awesome
Leave a Comment
Your email address will not be published. Required fields are marked *MySpeed
Thank you
Leave a Comment
Your email address will not be published. Required fields are marked *Leave a Comment
Your email address will not be published. Required fields are marked *