Microsoft: the number of web shells has doubled since last year
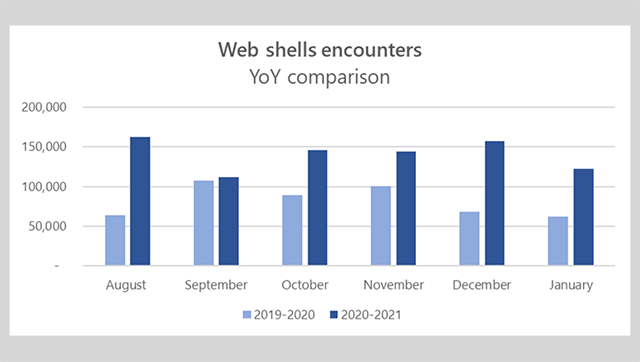
According to the Microsoft report, the number of malicious web shells installed on web servers has almost doubled since its last count in August 2020.
In a blog of the Redmond company, it was said there were roughly 140,000 web shells per month between August 2020 and January 2021 which were determined and this number was over double compared to that last year.
This situation is a result of a shift in how hackers view web shells. Web shells are considered a tool for script kiddies defacing websites and the go-to tool of DDoS botnet operators. They are now part of the arsenal of ransomware gangs and nation-state hackers alike and are crucial tools used in complex intrusions.
The versatility and accessibility are the reasons that make web shells become more popular. Web shells can be written in almost any programming language, therefore, they can be easily hidden inside a website's source code. As a result, it is difficult to detect them in the operation and often requires a manual analysis from a human operator.
In addition, hackers take advantage of web shells to execute commands on a hacked server via a graphical or command-line interface, providing attackers with a simple way to escalate attacks.
WEB SHELLS MORE PREVALENT AS MORE SERVERS ARE PUT ONLINE
As the corporate IT space has moved towards hybrid cloud environments, the number of companies running web servers has increased over the past few years, and, in many cases, public-facing servers often have direct connections to internal networks.
Having figured out this change in the makeup of corporate IT networks, attackers have amped up their attacks on public-facing systems. Web shells are crucial to provide a way to control the hacked server and then orchestrate a pivot to a target's internal network.
The US National Security Agency warned about these types of attacks in April 2020 when it published a list of 25 vulnerabilities installed in web shells.
Not only just warning about web shells used on public-facing systems but also about their use inside internal networks, where they are used as proxies to jump to non-public-facing systems.
Microsoft recommends a few basic actions as ways to keep networks secure:
-
Patch public-facing systems because most web shells are installed after attackers exploit unpatched vulnerabilities.
-
Extend antivirus protections to web servers in order to prevent web shell as well as increase Wifi signal strength
>>> See also: Unexpected reasons for poor speed check Wifi result
-
Network segmentation to limit the damage of an infected server to a small array of systems and not the entire network.
-
Audit and review log from web servers frequently, especially for public-facing systems, which are more vulnerable to scams and attacks.
-
Practice good credential hygiene. Limit the use of accounts with local or domain admin-level privileges.
-
Check your perimeter firewall and proxy to restrict unnecessary access to services, including access to services through non-standard ports.
.jpg)



0 Comments
Leave a Comment
Your email address will not be published. Required fields are marked *